This blog post is part of an ongoing series discussing the problem of operationalizing threat intelligence and how best to derive value from industry intelligence
Standing on the Shoulders of Giants
Overcoming common psychological hurdles in cybersecurity and cyber threat intelligence
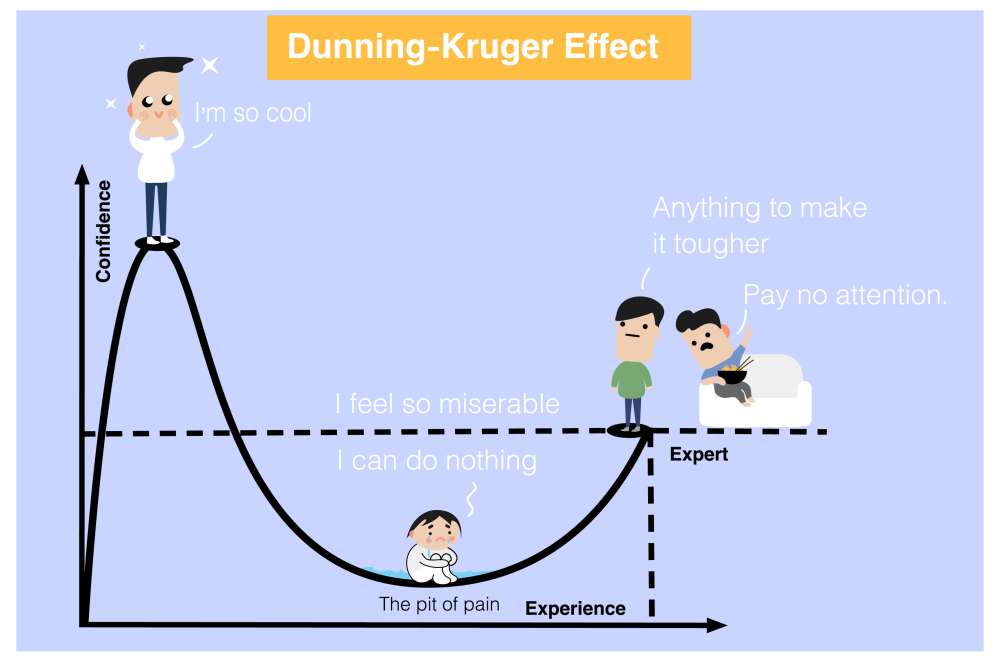
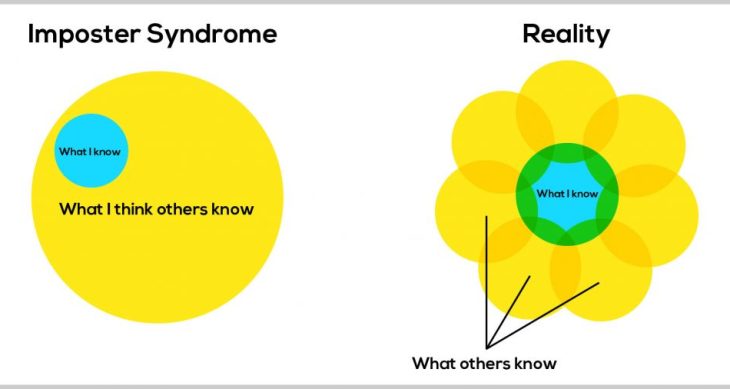
You’ve done it. You’ve finally found yourself immersed in the world that you so desperately were wanting to be a part of. You did the work, got through the classes, achieved that first certification that you thought was out of your reach. You applied to countless places, landed the interview, and got the job! You’re officially a “cybersecurity professional” now. This is a common start, and while not everyone has the same beginning, most have roughly the same middle journeys. Adventures rife with psychological hurdles and personal missteps one must get through to achieve their own version of greatness. Two of these hurdles that I’ve found almost every professional in the earlier to mid years of their career encounter are the Dunner-Kruger effect and the Imposter Syndrome.
Without knowing it, you’ve very likely stumbled into a journey of unending learning, surrounded by those that you feel you’ll never live up to. Astounding research by people across the globe on minutia you’ve never even heard of. Immense data sets you can only fathom how they were conceived, let alone collected and compiled. New vulnerabilities so obscure you wonder how the process even started. Attribution to criminals and state actors through incredibly thorough investigative means. How could you possibly compete?
All of this leads to the aforementioned psychological phenomenon. Both of which will likely come in peaks and valleys throughout your entire career. The Dunning-Kruger effect helps to explain those confident but know-nothing analysts that you hired fresh out of college (maybe this is you, right now) that will brag about their skills, but just can’t seem to put together a coherent incident write-up or threat assessment, let alone be given more responsibility within the overall cybersecurity program at an organization. It also helps to explain why some of your best analysts may lose confidence even amid them doing so many amazing things. At the far right of this spectrum are your truly enlightened, which often means a full understanding that it’s an impossibility to know everything or that that expectation of anyone is even realistic. Especially in this field, one that I would argue moves in a way like no other, you can’t possibly be on the forefront of it all.
The Imposter Syndrome is incredibly pronounced within the cybersecurity industry seemingly for similar reasons. Bug bounty hauls, CVEs, blogs, DFIR articles, CTFs, never ending alphabet soup of certifications, the list is almost never ending. You can choose to use this information as intelligence, or you can choose not to. You’re often given information to act on and use but often don’t even understand it yourself. If you can’t see how this fact alone would lead into a strong feeling related to the Imposter Syndrome, I doubt I’ll be able to convince you that it’s an issue in the industry at all. To achieve your greatness though is to be able to be adaptable enough to survive and bring value back to your organization through using this information, however it can be achieved.
This is where the title of the post comes into play. Why strive so hard to be an “expert” in what are essentially disparate but tangentially related disciplines? This industry comes out with so much great intelligence, resource building, and shared learning. Use it! The folks out here spending countless hours going through the minutia of some obscure protocol to churn out a usable exploit are doing it for their own good, but you can use that knowledge, so do it! Stand on the shoulders of these niched giants. We shouldn’t let the fact that individuals are better than us at any given niche or portion of the industry scare us into feeling unconfident about our own plethora of skills. Besides, most companies aren’t looking to hire someone that is so deep in the weeds of a particular minute portion of the industry, while admirable, most would rather you be an adaptable generalist that can help relay pertinent details in a timely manner.
Never feel like a fraud for not understanding something in this field. Cybersecurity has become too nuanced, abstract, and obscure for its own good. Comically simple things are still used by modern adversaries in 2021 and there’s very little that most organizations can do to stop it. Why would you feel like a fraud because someone found an obscure vulnerability in some memory side-loading nonsense (Spectre, etc.)? While we should all appreciate the research and the hypothesizing that comes with it, there should be an understanding that it’s for nothing but research until it’s actively used, and at that, what are you going to do about it? At best, you’re going to patch, at worst you’ll do nothing. Without the research or knowledge, or someone with a finger on the pulse, how would your organization know this is an issue? The accountants aren’t going to bring this up, nor are the operations people. This is where you come in, standing on the shoulders of giants.
The utilization of research and open-source intelligence (shared learning) is absolutely a skill. Never discount something of value just because you didn’t conceive of it yourself or you think it’s “unoriginal” to use the research of others. Learning to ask good questions that spawn investigations can be paramount to uncovering vast amounts of misconfigurations or outright ineptitude within your given organization. If nothing else, you can give your analysts and employees awareness of common, modern threats that you otherwise may have been unaware of.